
Running Feature: Quantum Key Distribution, Protecting the Future of Digital Society (Part 1) The Principles of Quantum Key Distribution Technology and the BB84 Protocol | DiGiTAL T-SOUL | TOSHIBA DIGITAL SOLUTIONS CORPORATION
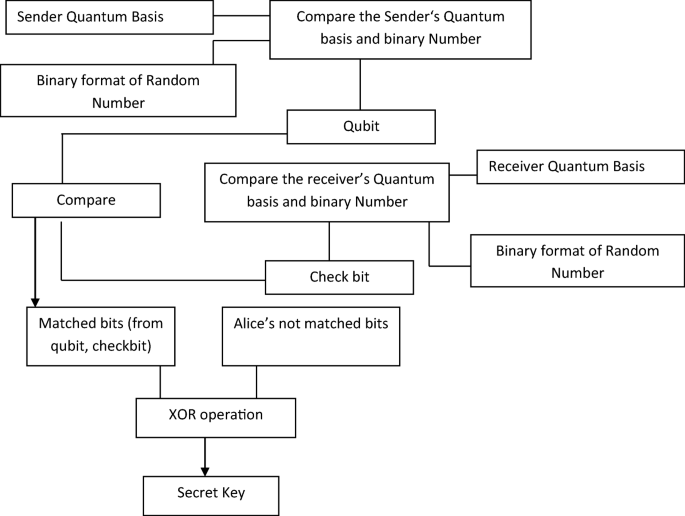
Enhanced BB84 quantum cryptography protocol for secure communication in wireless body sensor networks for medical applications | Personal and Ubiquitous Computing


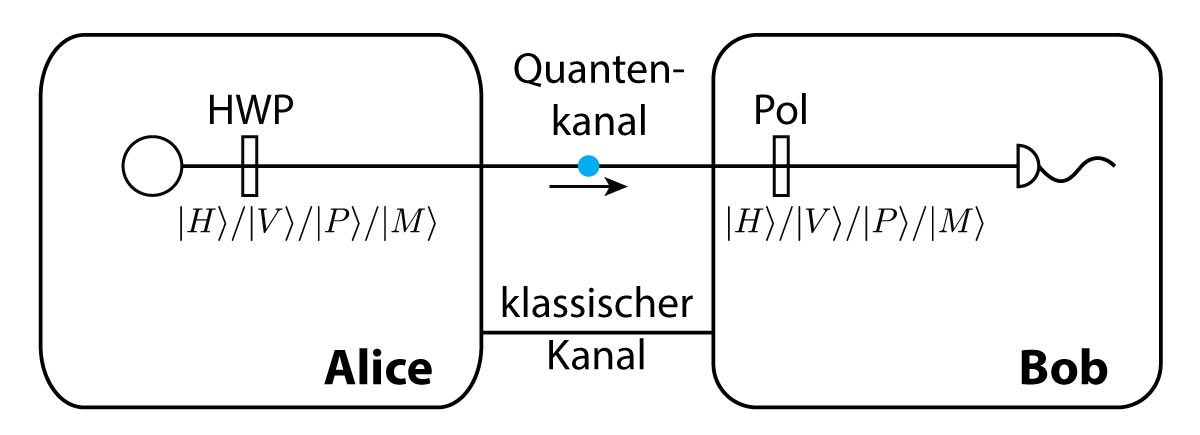


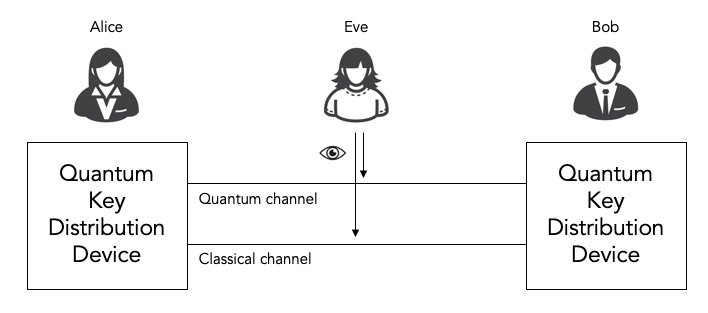

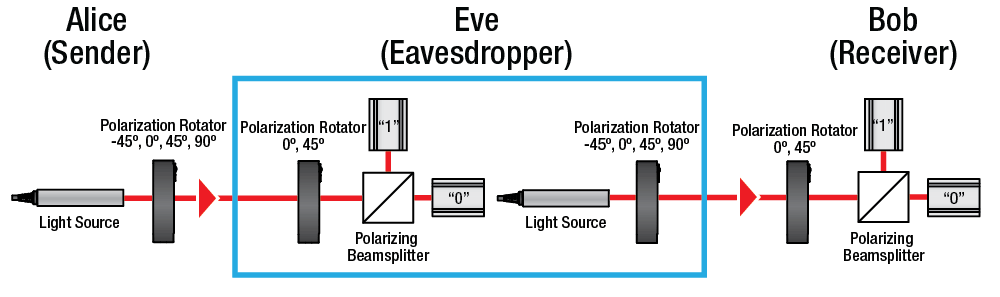


![PDF] Is Quantum State in BB84 Protocol Really Unclonable? 1) | Semantic Scholar PDF] Is Quantum State in BB84 Protocol Really Unclonable? 1) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1d0e2facfd2c79db6f100c4b2c8a81153475a940/2-Figure1-1.png)






![Schematics of the BB84 protocol. [3] | Download Scientific Diagram Schematics of the BB84 protocol. [3] | Download Scientific Diagram](https://www.researchgate.net/publication/2200757/figure/fig2/AS:667773277577234@1536220964868/Schematics-of-the-BB84-protocol-3.png)

![PDF] Simulation of BB 84 Quantum Key Distribution in depolarizing channel | Semantic Scholar PDF] Simulation of BB 84 Quantum Key Distribution in depolarizing channel | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dadec5fec103285dd0dcc77bdab01714746f18d0/1-Table1-1.png)