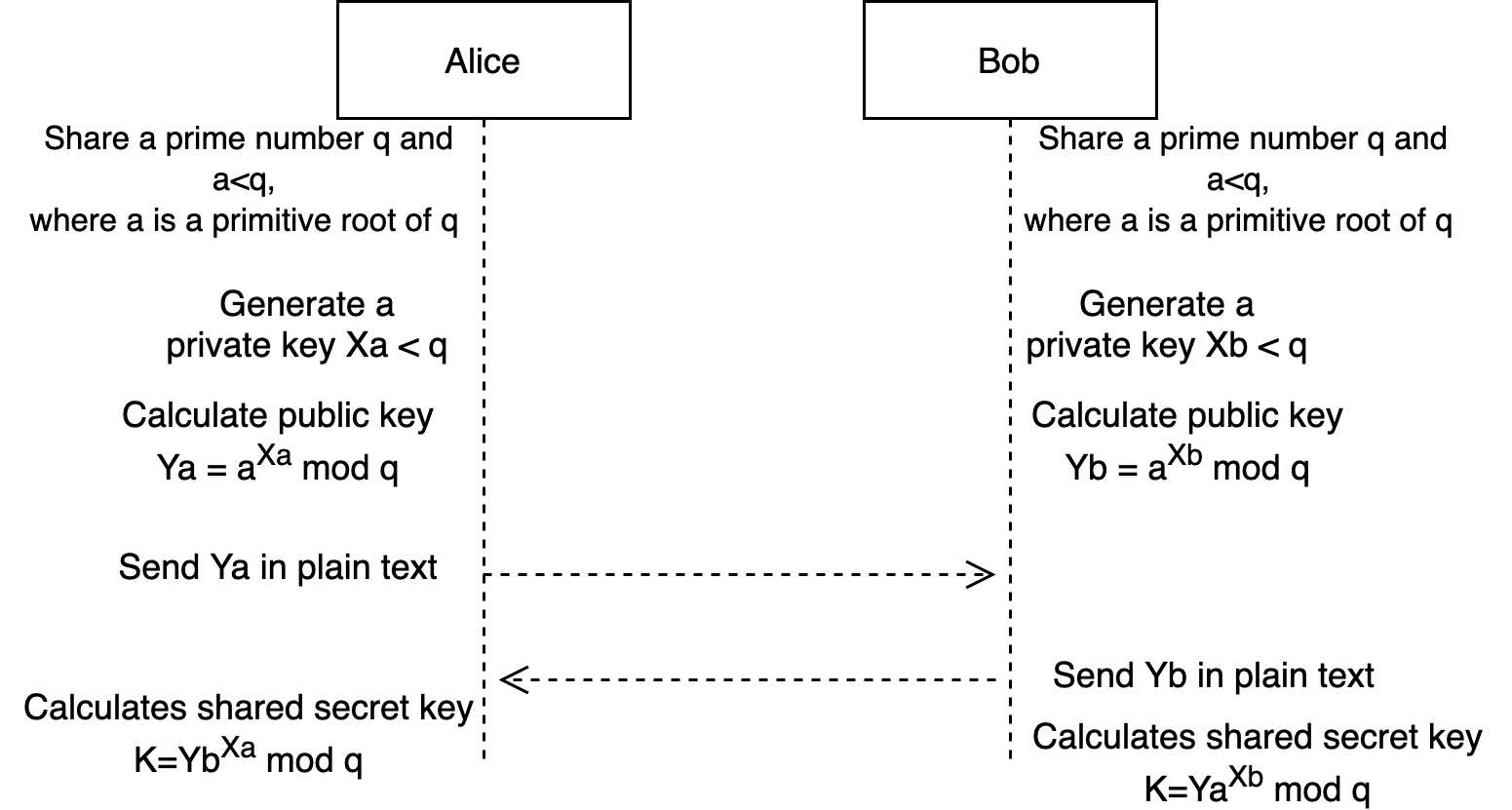
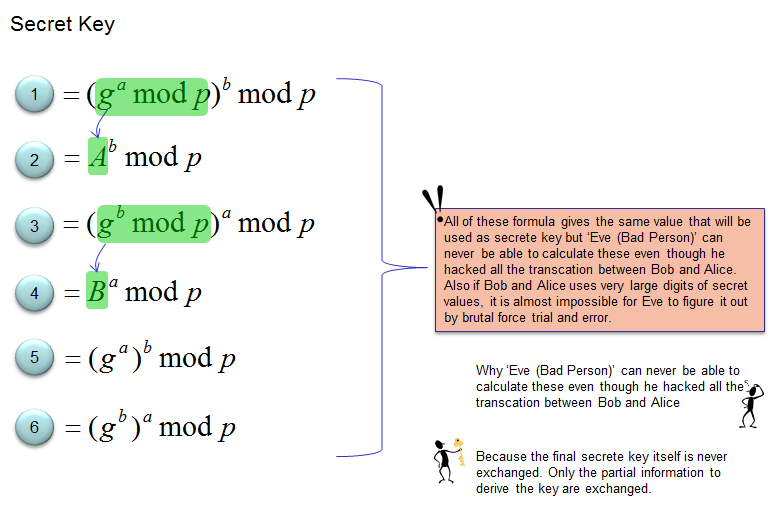
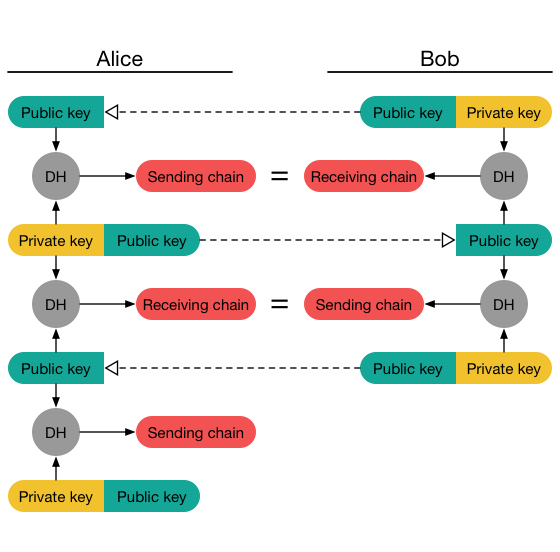
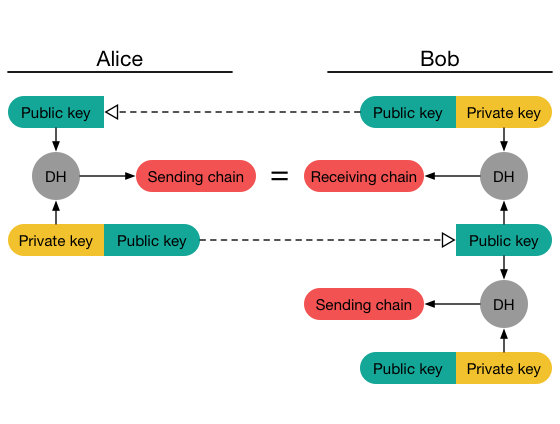
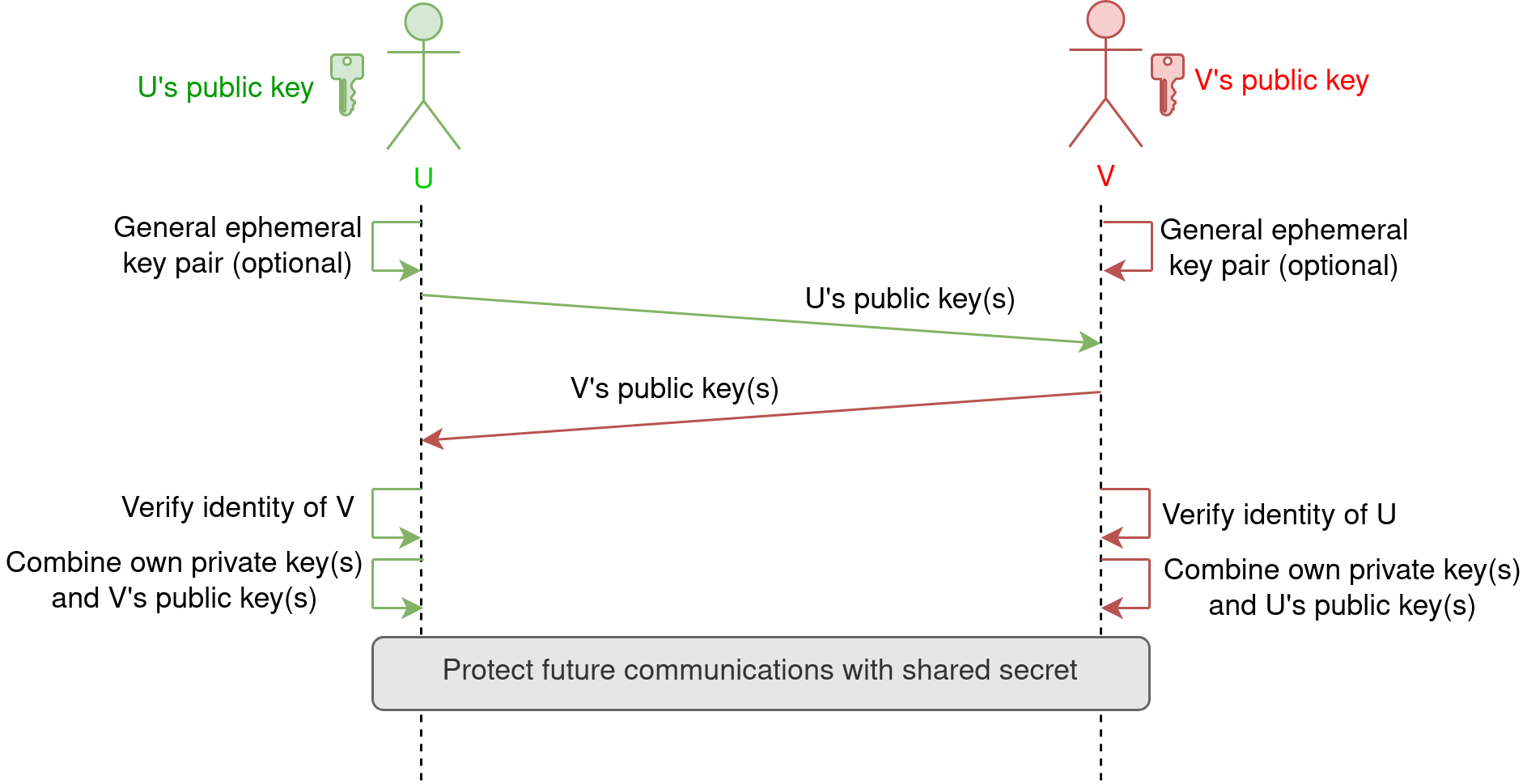
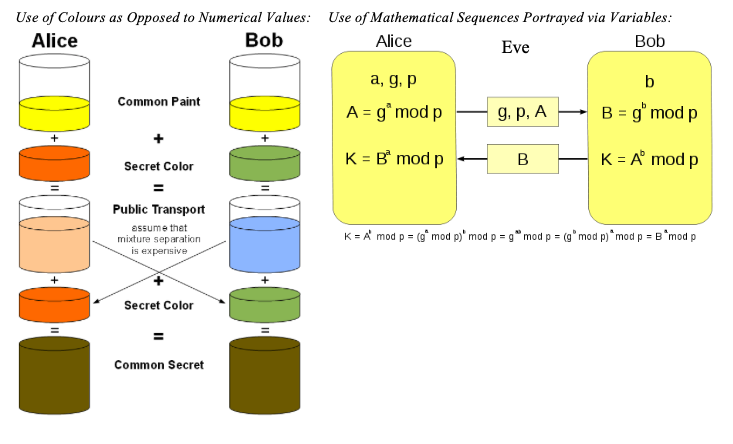
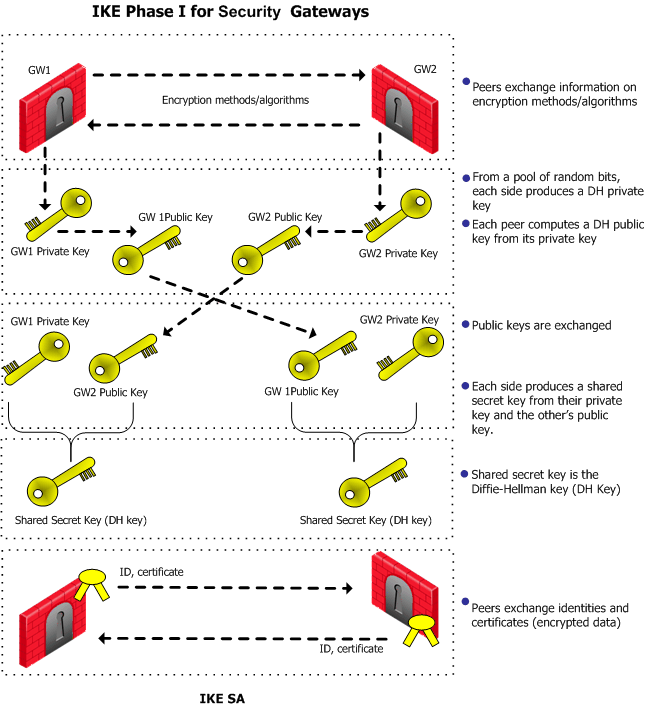
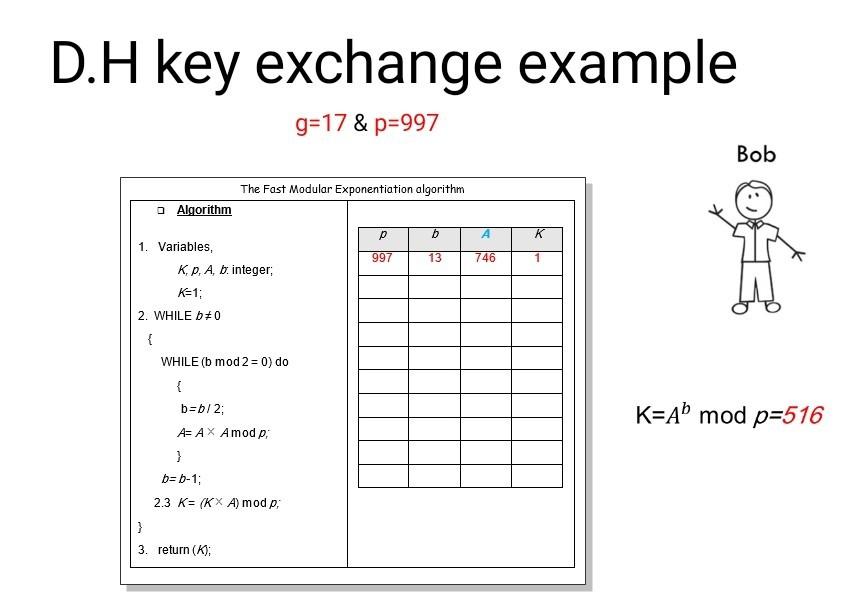
A man in the middle (MITM) attack over Diffie-Hellman (DH) protocol.... | Download Scientific Diagram

security - Is it possible to "hack" Diffie-Hellman by knowing the prime number and the generator parameters? - Stack Overflow
Diffie-Hellman Key Exchange - the MAGIC that makes it possible - Cryptography - Practical TLS - YouTube