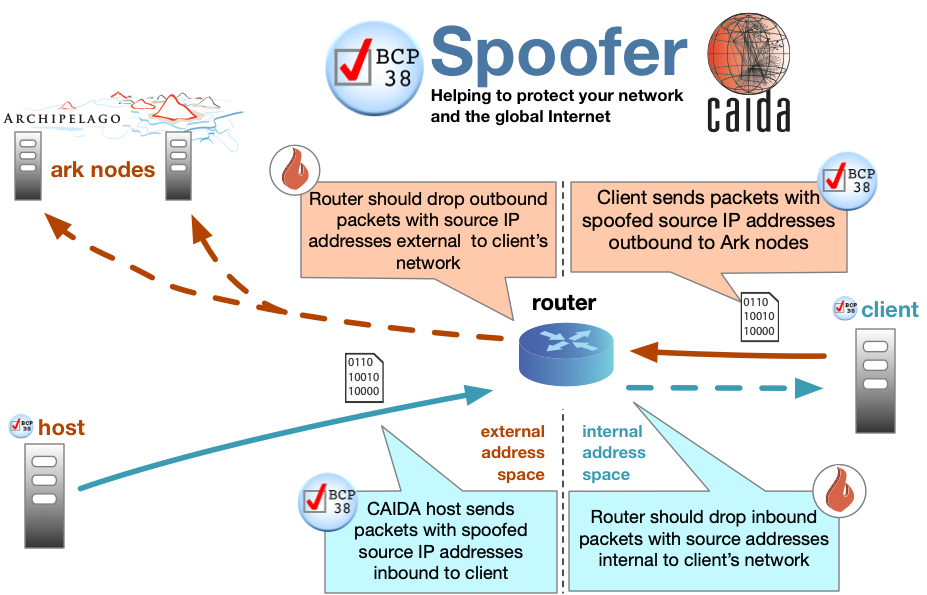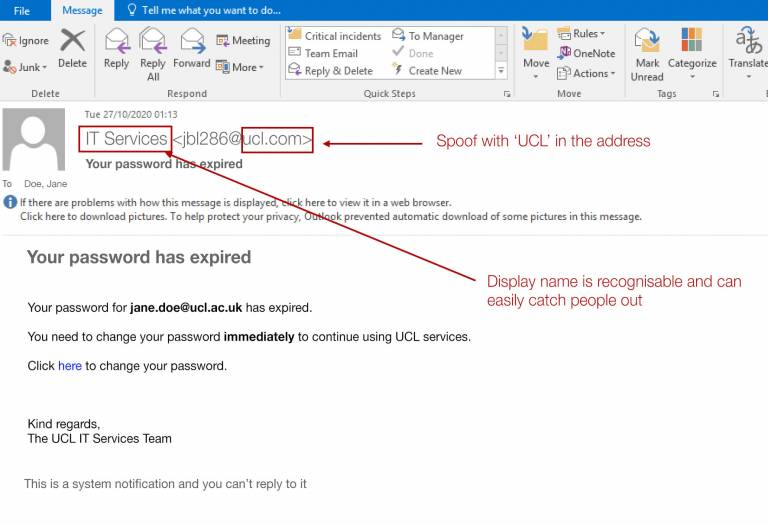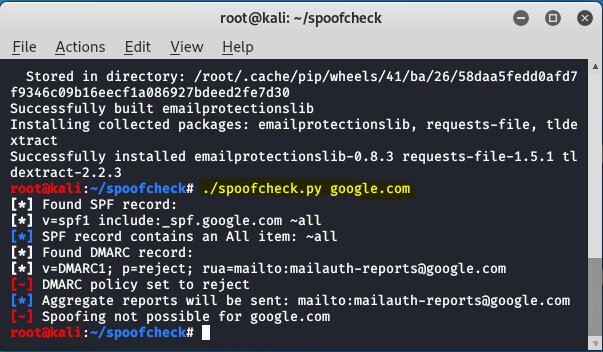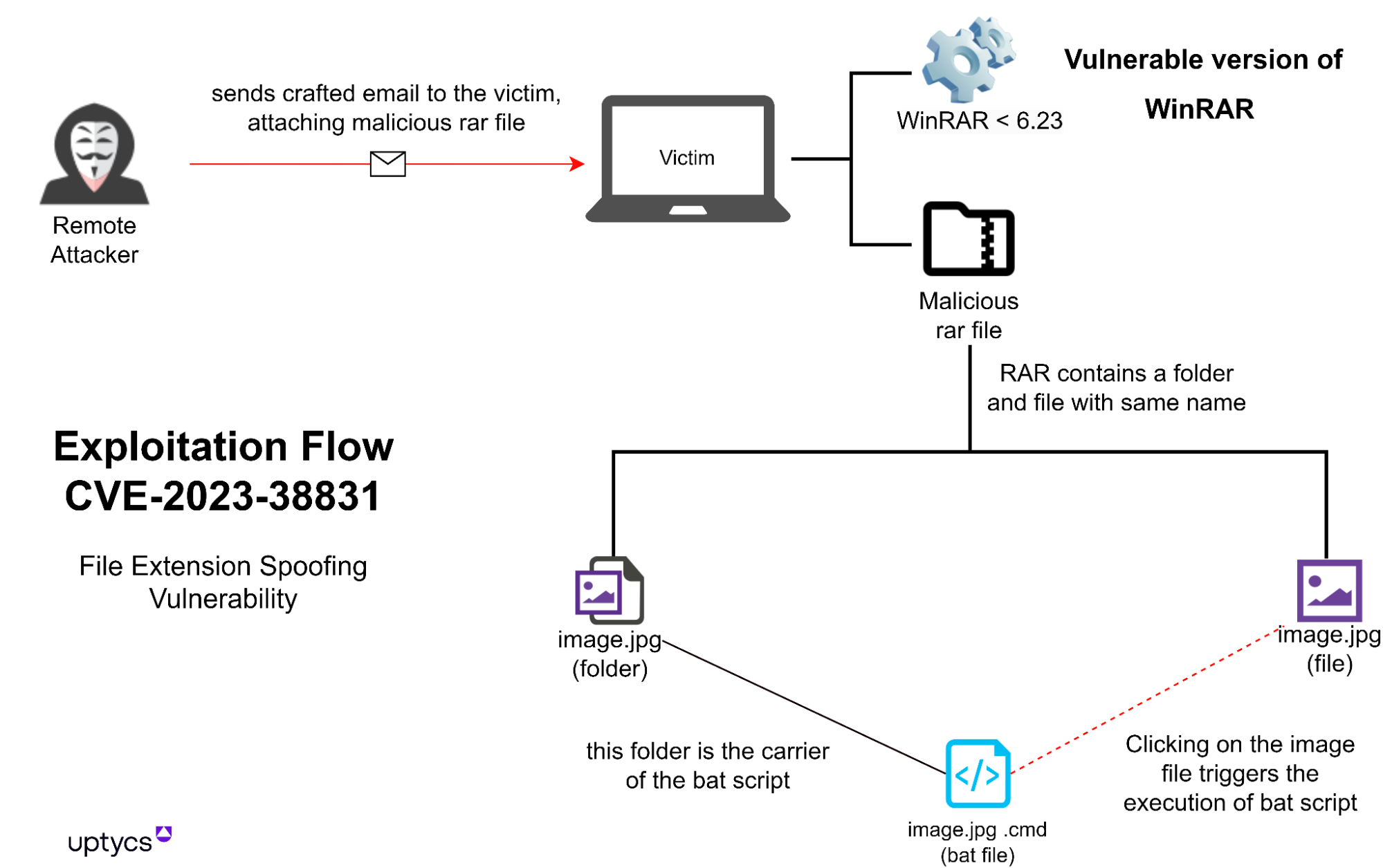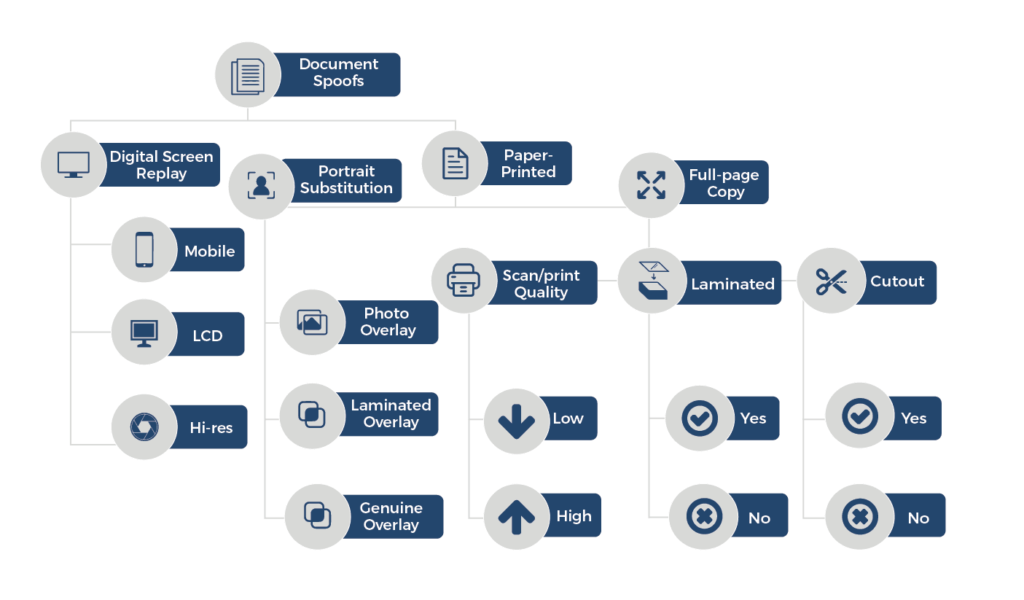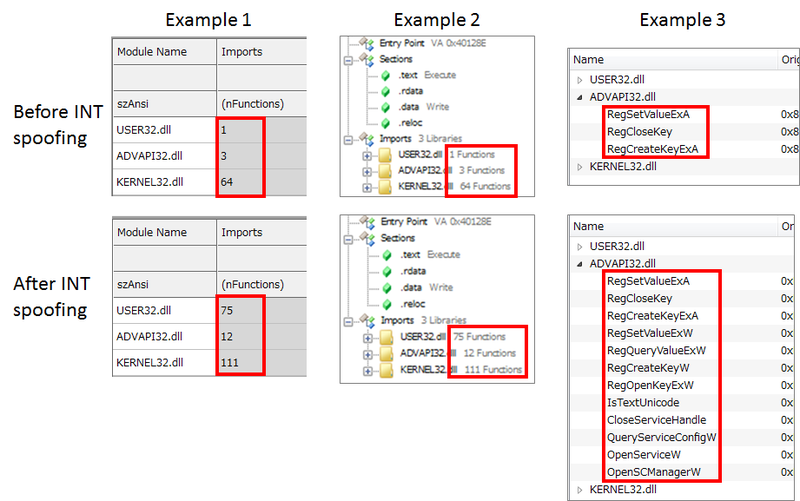
Anti-analysis technique for PE Analysis Tools –INT Spoofing– - JPCERT/CC Eyes | JPCERT Coordination Center official Blog

USENIX Security '22 - Oops... Code Execution and Content Spoofing: The First Comprehensive Analysis - YouTube
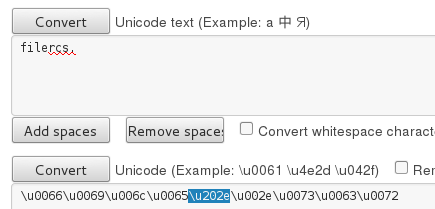
GitHub - moom825/batch-extention-spoofer: spoof an extension of any file by using U+202E Unicode character
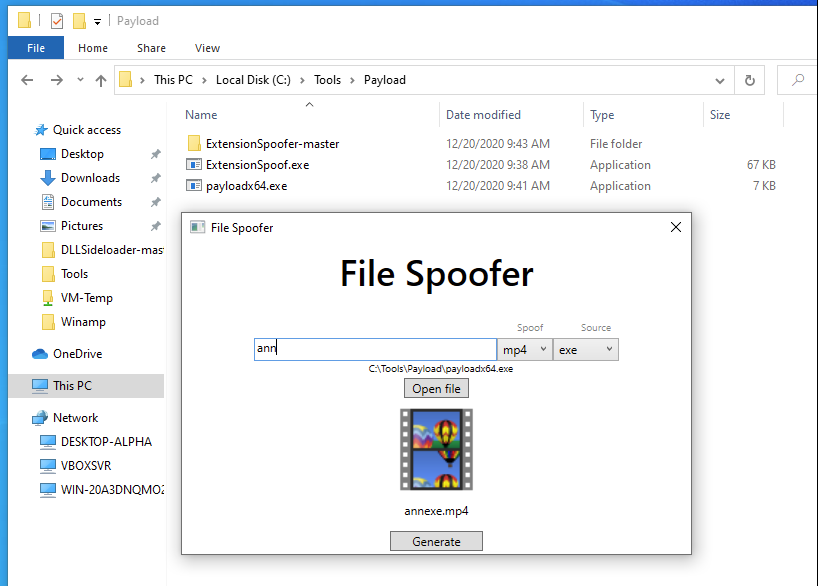
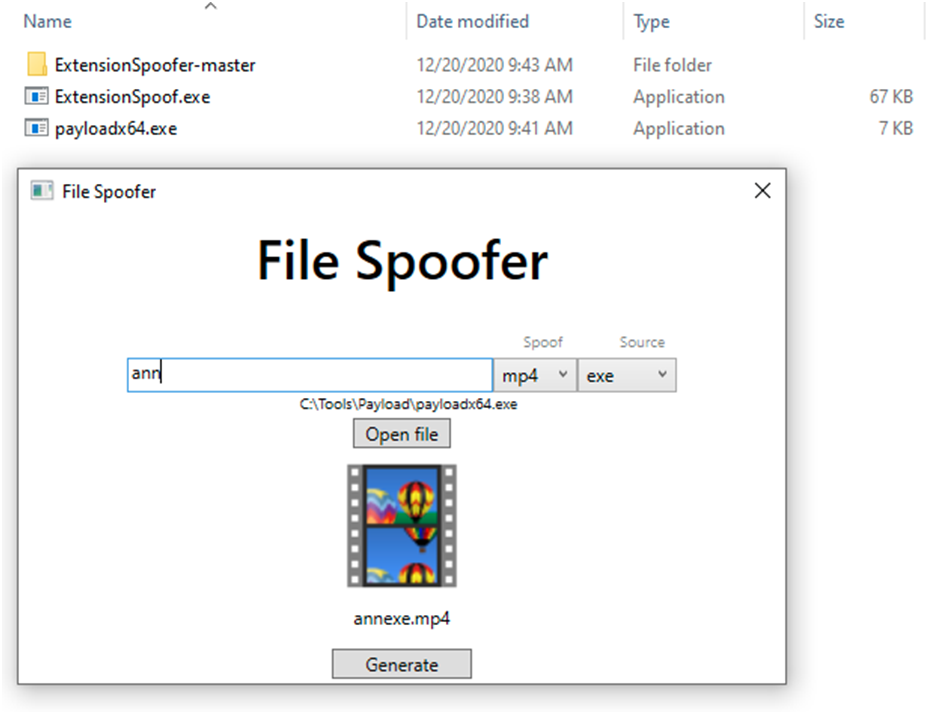
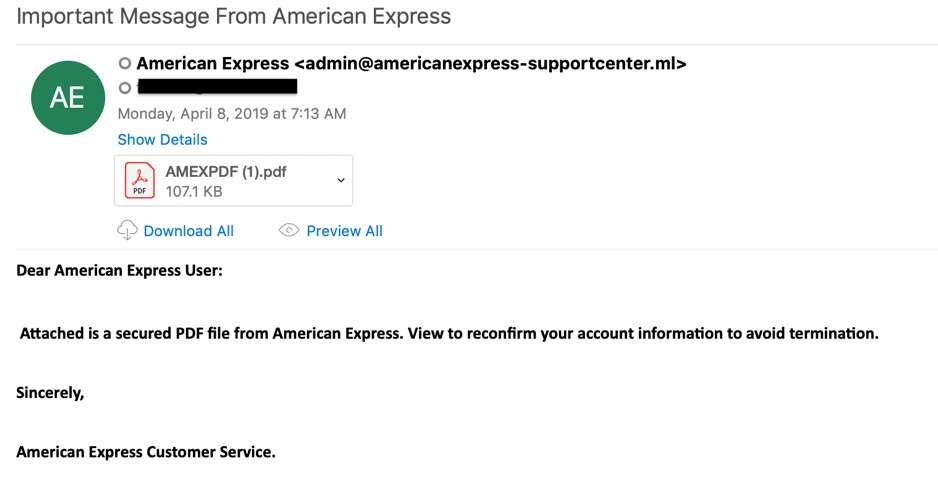
GitHub - Loubaris/Extension-Spoofer: Spoof your payloads/codes extensions into safe extensions | FUD