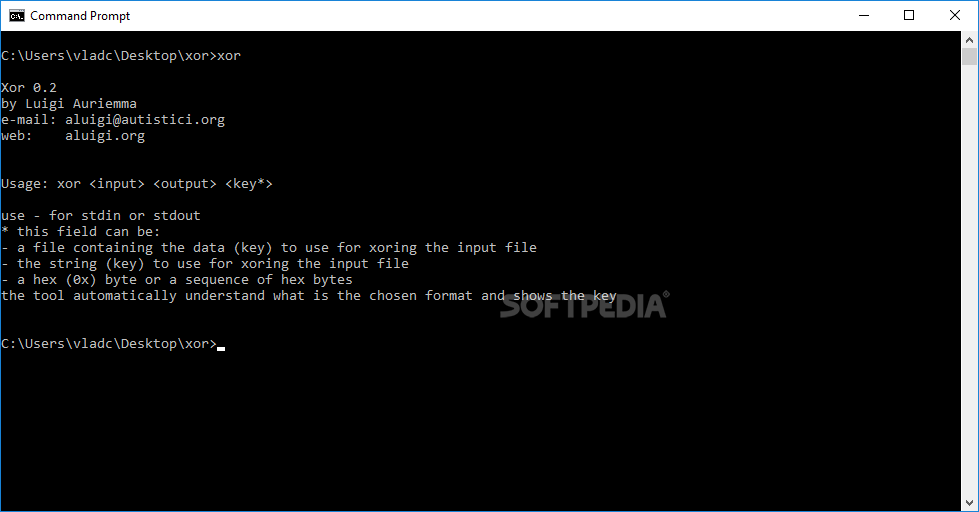
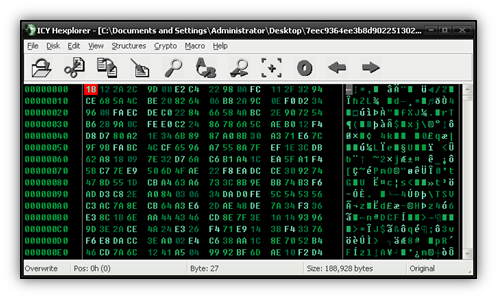
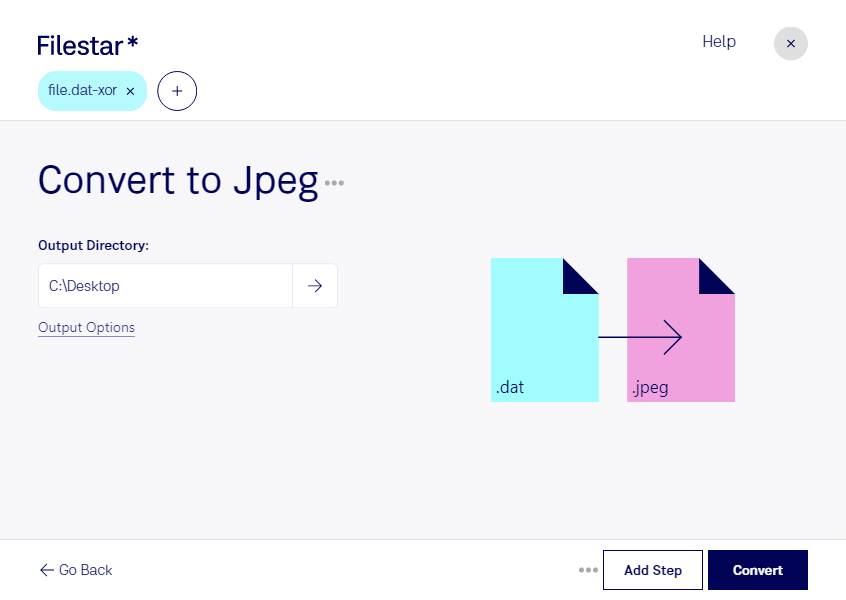
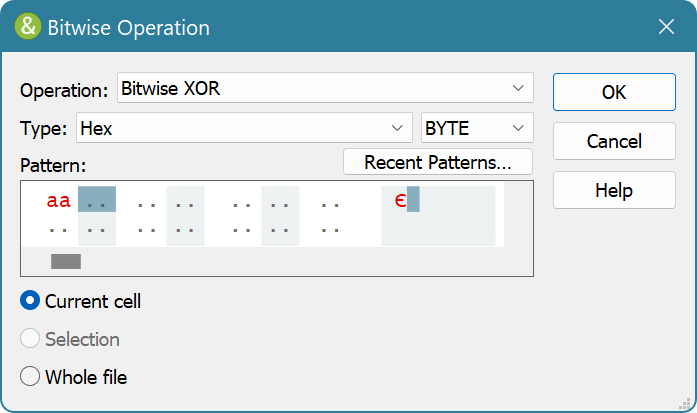
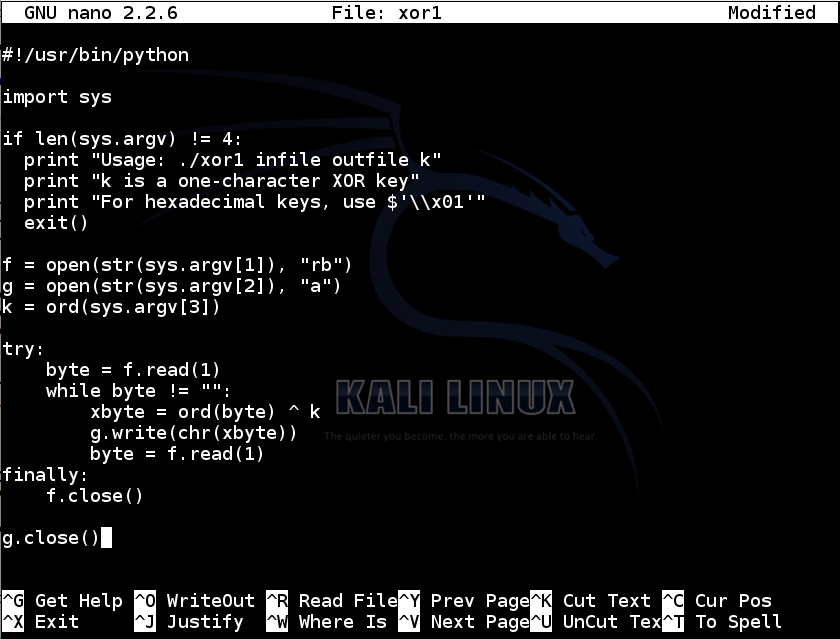
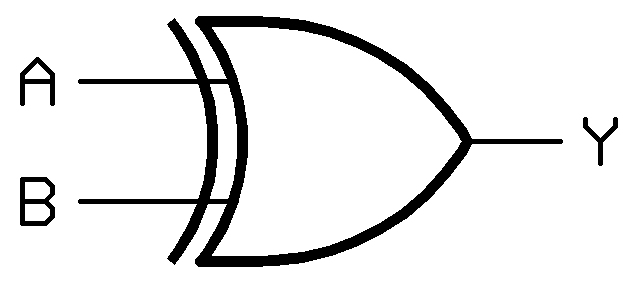
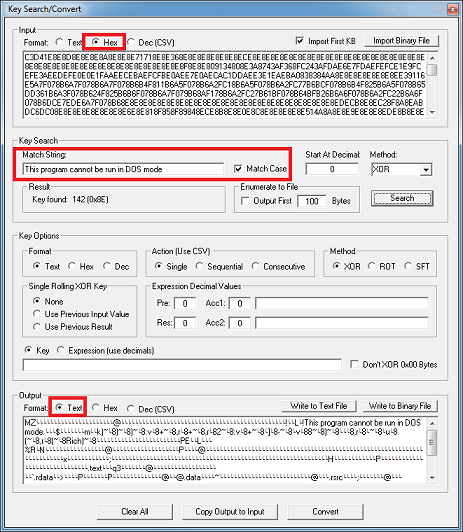
GitHub - FanaticPythoner/ProjectXOR: Heavily multithreaded tool for bruteforcing XOR Encryption. Multiple options available for specific bruteforcing rules.
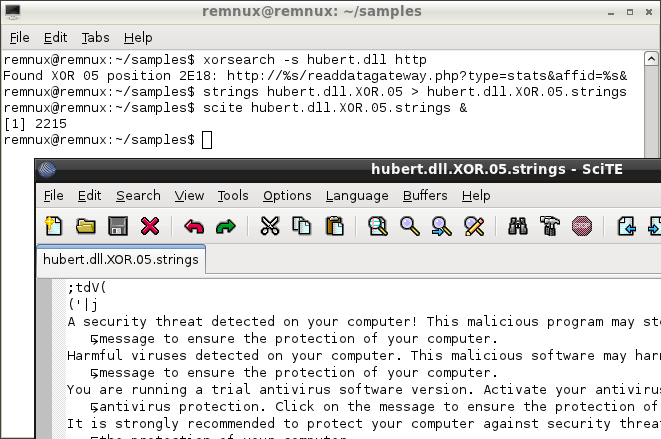
SANS Digital Forensics and Incident Response Blog | Tools for Examining XOR Obfuscation for Malware Analysis | SANS Institute
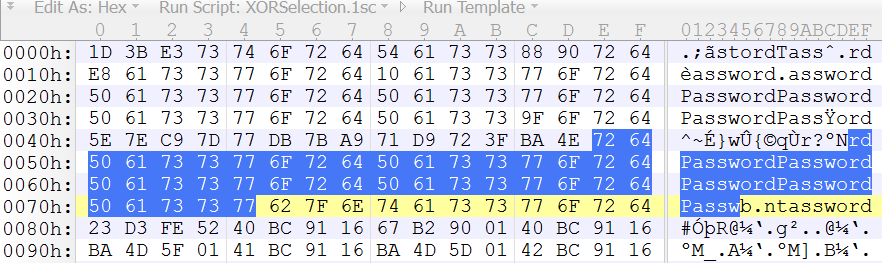
GitHub - mightbesimon/XOR-file-encryption: Encrypts files with a password byte-by-byte using a XOR cipher

File Type Identification and Its Application for Reversing XOR Encryption | Crucial Security Forensics Blog